Please be aware that this page covers downstream webhooks. These are webhooks
that Kombo sends to your system for events like new integrations or finished
syncs. If you try to understand webhooks that Kombo receives from the
connected ATS/HRIS such as Personio or Recruitee, check out this
page.
Enable Webhooks
You can configure your Kombo webhooks in the dashboard directly in the webhooks tab. After creating the first webhook, a random webhook secret will be generated and shown. You can learn how to use it in Validate the data.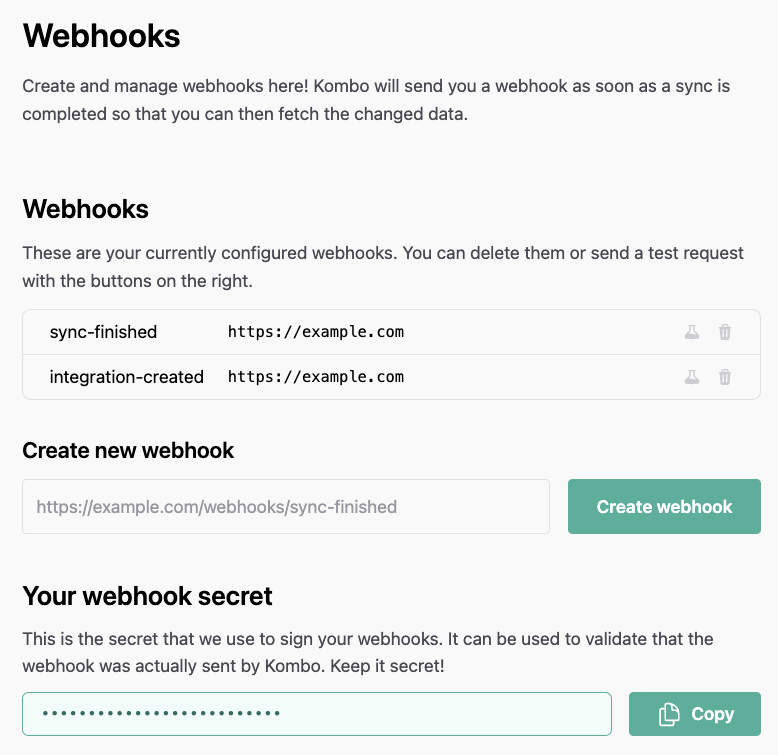
Available webhooks
Data changed
We send adata-changed webhook every time data changes in Kombo. This includes
changes from regular syncs as well as updates from upstream webhooks.
Read more about the modern fetching approach here.
We trigger this webhook, when we receive a change. To speed up delivery of
changes to Kombo, ensure that upstream webhooks are enabled for the
integration. If upstream webhooks are not enabled or not supported,
notifications are sent after the next scheduled sync (latency equals the sync
frequency).
updated_after filter.
This webhook is useful to fetch data from Kombo into your system. Read more
here.
We will only ever send you a data-changed webhook if there are changes to the data.
data-changed
data-changed with a 30-second window by default. This means
that you will at most receive one data-changed webhook every 30 seconds.
When the webhook is triggered for the first time, we send it out immediately.
After that, we will wait 30 seconds, during which we will collect all events and
send them as a single webhook, thereby starting another 30-second cooldown
window. We do not wait for syncs to finish before sending out the webhook;
instead, we may send you multiple webhooks during a single sync to ensure you
receive changes as soon as possible.
Sync finished
Thesync-finished webhook is sent every time a sync finishes, regardless of
the sync state. Possible values for sync_state are:
SUCCEEDEDThe sync finished successfully.PARTIALLY_FAILEDThe sync succeeded but had non-fatal errors. Kombo will take care of it.FAILEDThere was a critical error during the sync and the sync did not finish. If this happens, we get an alert and will look into the issue to fix it ASAP.TIMED_OUTThe sync timed out before completion. This happens rarely and will cause an immediate and automatic restart of the sync. Kombo will be notified and look into the issue ASAP.CANCELLEDThe sync was actively canceled by Kombo. This happens very rarely, has no negative side-effects, and if it does happen, we will schedule a new sync shortly after.AUTHENTICATION_FAILEDThe authentication of the connection is incorrect. Please check the Kombo dashboard for further steps.
The
sync_started_at field represents when Kombo started syncing data from
the connected system, not when you should start fetching from Kombo. Do not
use this field as your updated_after parameter when fetching data.
Otherwise, you might risk missing data that was created/updated via webhooks
before the sync started.sync-finished
Integration created
Theintegration-created webhook is sent for every integration that is created.
Please react to this webhook event by adding the integration to your database
or by performing any other business logic that is required when an integration is
created.
integration-created
Integration deleted
Theintegration-deleted webhook is sent when an integration is deleted.
Please react to this webhook event by removing the integration from your database
or by performing any other business logic that is required when an integration is
deleted.
integration-deleted
Connection flow failed
Theconnection-flow-failed webhook is sent whenever an error occurs during the
connection flow. These errors could, for example, originate from a user entering
incorrect credentials or from a mismatch between the required and supplied API
permissions.
This is not an alert-type webhook, but should instead be used to collect data
and get insights into user behavior. The connection flow can still be
successfully completed after this webhook is sent.
You can check whether the connection flow ended successfully by following the
link under log_url. Additionally, the log will display the exact errors your
customer ran into, which you can use to provide support if needed.
connection-flow-failed
Assessment order received
Theassessment:order-received webhook is sent every time an assessment is
ordered for a candidate from within an end-customer’s tool.
assessment:order-received
Integration state changed
Theintegration-state-changed webhook is sent when the status of the
integration changes. Use this to detect stale credentials and to reconnect your
customer.
Possible values for the "state" key include:
ACTIVEThe integration is active and working.INVALIDThe connection requires reconnection in order to work again.INACTIVEUpon your request, Kombo support can mark the integration as inactive.
integration-state-changed
Validate the data
Anyone could post data to your webhook URL. That’s why we’re signing each request with a secret specific to your Kombo account. This secret is called the Kombo Webhook Secret and you can find it on the Kombo dashboard. Each valid webhookPOST request from us will include the X-Kombo-Signature
header. To validate it, carefully follow these steps:
- Decode the
X-Kombo-Signatureheader frombase64urlencoding (without padding) to raw bytes. - Compute the HMAC-SHA256 over the raw JSON request body (Kombo encodes this using two-space indentation) with your Kombo Webhook Secret as raw bytes.
- Compare the decoded signature bytes to the computed HMAC bytes using a
constant-time comparison function (like Node.js’s
timingSafeEqual) to protect against timing attacks.
Testing webhooks
The list of all created webhooks has two buttons on the right. One is for deleting the webhook, the other is for sending a test request. This test request will contain dummy data but will use the correct data schema. Be careful when using this feature in production! It will send invalid data to your webhook.Testing locally
For local development, you can use a service like localtunnel or ngrok. These tools allow you to expose a local port through a public URL provided by them. The setup is very straightforward: Once you’ve started a tunnel, simply add the provided URL as a webhook in the Kombo dashboard. You can then send test requests to validate that your endpoint is working properly.Retry behavior
If your webhook endpoint does not acknowledge the webhook (returns an error or does not respond), Kombo will automatically retry the delivery. This ensures reliable webhook delivery even when your endpoint is temporarily unavailable.Retry attempts
Kombo will retry failed webhook deliveries up to 5 times before giving up. Each retry uses exponential backoff with the following delays:- After 1st failure: 1 second
- After 2nd failure: 2 seconds
- After 3rd failure: 4 seconds
- After 4th failure: 8 seconds
- After 5th failure: 16 seconds
Error conditions that trigger retries
Kombo will retry webhook deliveries for the following error conditions:- Rate limit errors (HTTP 429): Retries respect
Retry-Afterheaders when provided - Server errors (HTTP 5xx): Temporary server errors that may resolve on retry
- Connection errors: Network timeouts, connection resets, DNS failures, and other transient network issues
- Cloudflare errors (HTTP 409 with Cloudflare 1018 error): Temporary Cloudflare blocking errors
Error conditions that do not trigger retries
The following errors will not trigger retries, as they indicate permanent failures:- Client errors (HTTP 4xx, except 429): These typically indicate issues with the webhook configuration or request format
- DNS not found (ENOTFOUND): The webhook URL cannot be resolved
Best practices
To ensure reliable webhook delivery:- Respond quickly: Return a 2xx status code as soon as you’ve received and validated the webhook, even if you process it asynchronously
- Handle idempotency: Webhooks may be delivered multiple times due to retries, so ensure your webhook handler is idempotent
- Monitor webhook logs: Check the Kombo dashboard for webhook delivery failures and retry attempts